Information gathering
Introduction:
Information gathering / footprinting / reconnaissance, refers to collecting every possible piece of information concerning a target and the target network. The information required maybe available through publicly available personal information or via a more confidential source or both. This information helps in identifying possible ways to gain access to any target network and system. This means using the information collected to identify vulnerabilities within the target network and system, which can be exploited exploited in order to gain access.
Footprinting is achieved by performing social engineered attacks or attacks on the system or network or through other techniques. The deeper the information regarding a target, the more accurately the hacker can reduce the target area and pinpoint the vulnerability. The main purpose of of this phase is to keep interactions with the target discreet in order to gain information without being detected.
Pseudonymous footprinting:
This refers to footprinting through online sources. Here, information about the target is shared by post under an assumed name. This type information is shared with the real credential to avoid trace to an actual source of information.
Internet Footprinting:
Here, information is gathered from the internet, using resources such as google search, google hacks, as well as other search engines apart from google.
Types of Information Gathering:
Within information gathering, there are two types:
- Passive information gathering
- Active information gathering
Passive information gathering:
This type of information gathering happens before active information gathering. The main aim of passive information gathering is to collect information about the target without establishing direct interaction with the target. This being the case, the chances of being detected are extremely low. Almost all the information gathered here is open to the public.
Some of the resources include:
OSINT:
Open Source Intelligence - it is the publicly available information on the internet. Through OSINT gathering information of the collected from the company website, social media sites, domain name system (DNS) information, blogs, and so on.
Search Engines:
This is the most basic type of footprinting as well as the most responsive. Search engines provide information about any entity that is searched for. Moreover, search engines are openly accessible through any web browser, such as Google Chrome, Firefox, etc.
As an example, publicly available information such as that about any company, including its head quarters, who the CEO is, its valuation, parent organization, the date on which the organization founded, the founder's name, and more.
Advanced Google Hacking Techniques:
Google Hacking Techniques are a set of operators which can provide results which are more accurate and appropriate than generic operators.

Social Networking sites:
Social networking sites can be used o gather information about targets via psychological manipulation. This is done by getting close to the victim in order to get extract data from them.
Active information Gathering:
Active information gathering is when you are interacting directly with the target system in order to collect information about the target. This refers to collecting information such as open port information, information about the OS the machine is running, banner-grabbing, DNS enumeration and discovering vulnerabilities within the target machine. The downside here is the chances of being detected are considerably higher than passive information gathering.
Network:
Footprinting networks is one of the important types of footprinting. Since computer networks are what allows computers to communicate with one another, it is very useful to gather information about the network which a computer is connected to, in order to access it. There are many types of tools available which can be used for network footprinting. Some are as follows:
- Whois
- Ping
- Nslookup
- Traceroute
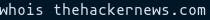
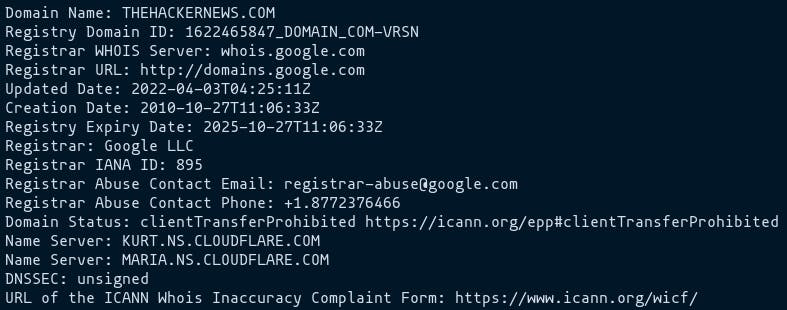
Whois:
This tool is used to find out the complete contact information associated with the person, company or entity that registered the domain name. A typical whois record will contain the following information:
- The name and contact information of the registrant: The owner of the domain.
- The name and contact information of the registrar: The organization that registered the domain name.
- The registration date.
- When the information was last updated.
- The expiration date.
Ping:
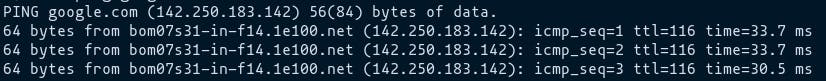
This tool is used to check the connectivity between server and host/server. it takes either the url or IP address of a site as input and send data packets to the specified address with the message PING and gets a response from the website in case of successful connectivity. Ping uses ICMP(Internet Control Message Protocol) to send an ICMP echo message to the specified host if that host is available then it sends ICMP reply message.

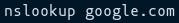
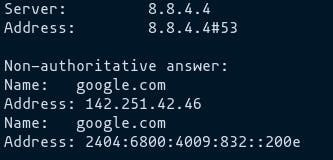
Nslookup:
Nslookup (stands for “Name Server Lookup”) is a command line utility for getting information from the DNS server. It is a network administration tool for querying the Domain Name System (DNS) to obtain domain name or IP address mapping or any other specific DNS record. It is also used to troubleshoot DNS-related problems.
Traceroute:
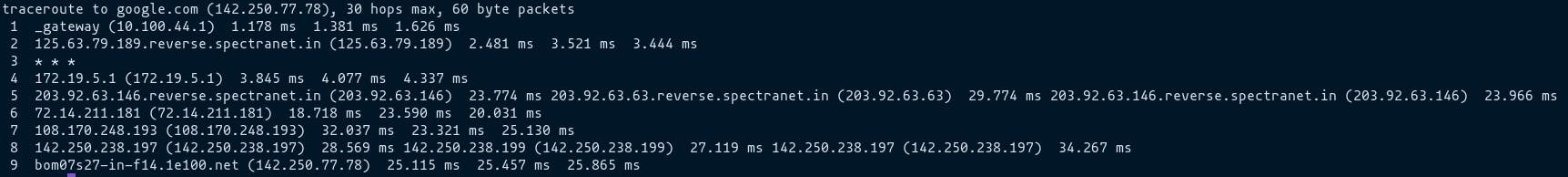
Traceroute is a tool which is used to trace the route a packet takes in order to reach the host.
Tools used for active information gatehring:
- Nmap
- Nikto
- Dnsenum
- Netcat
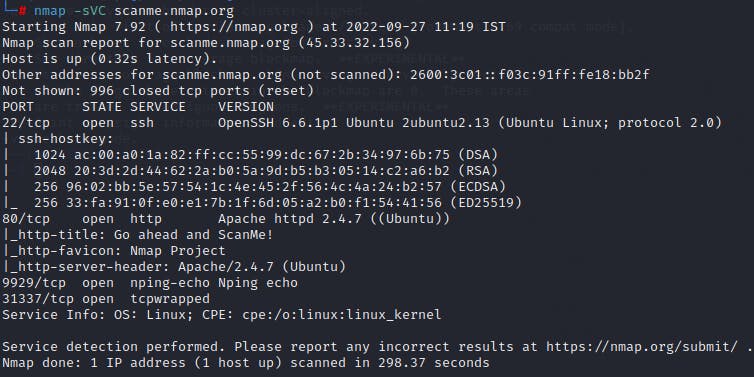
Nmap:
Nmap is one of the most popular port scanners which is free and open-source. It is a port-scanner and network mapper which uses a PING sweep in order to discover new hosts within a network as well as identify open and closed ports within known devices within the network.
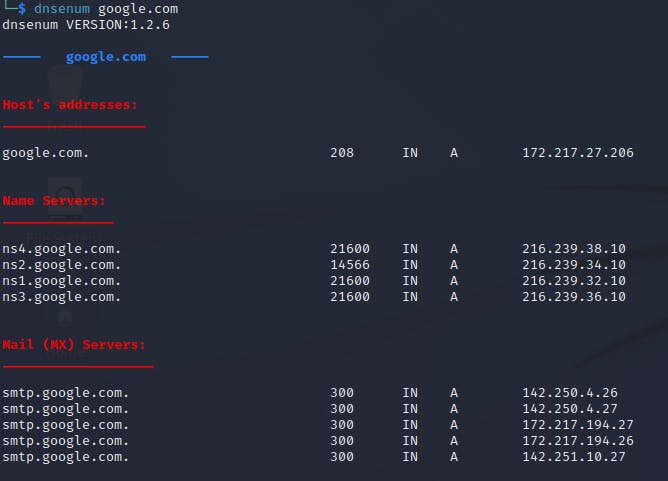
Dnsenum:
DNSEnum is a command-line tool that automatically identifies basic DNS records such as MX, mail exchange servers, NS, domain name servers, or the address record for a domain. It also attempts zone transfers on all identified servers, and it has the ability to attempt reverse resolution (that is, getting the hostname given an IP address) and brute forcing (querying for the existence of hostnames in order to get their IP address) of subdomains and hostnames.
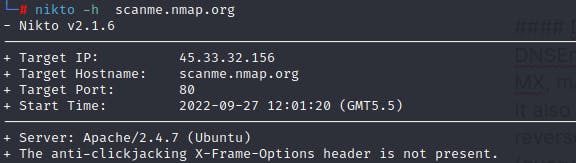
Nikto:
Nikto is an open-source web server scanner which performs test against web-servers in order to find vulnerabilities and present a detailed. It can check the server for configuration items such as presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software.
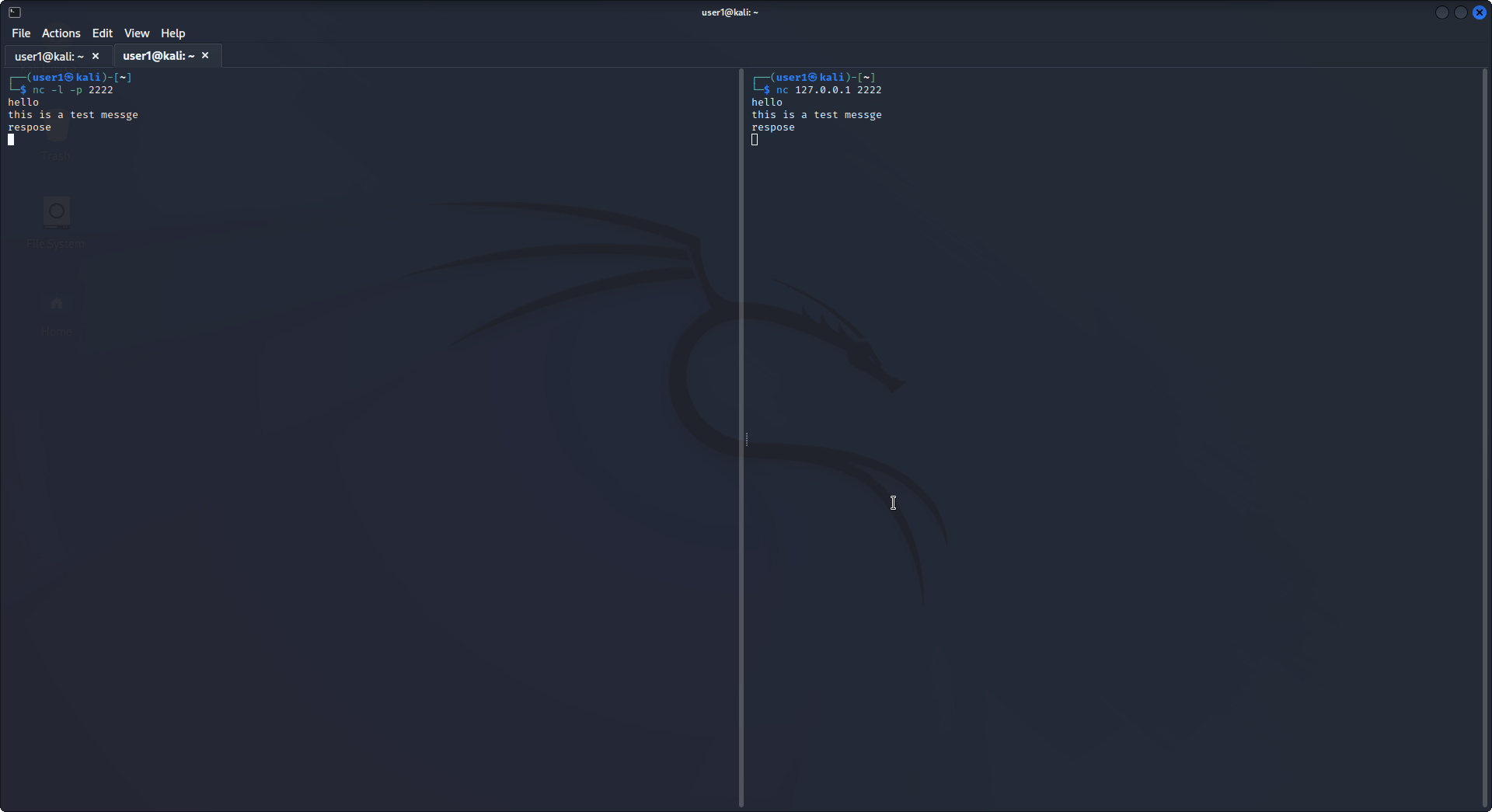
Netcat:
Netcat is a powerful command line tool that is used to perform network monitoring tasks, security related tasks as well as network tasks. It is used to read and write data between two computer networks, which can take place through either TCP or UDP.
Netcat is considered a Swiss Army Knife for networking tools since it has a rich collection of troubleshooting and networking features.
Some of its features are as follows:
- Operation related to TCP, UDP or UNIX-domain sockets
- Port Scanning
- Port redirection
- open Remote connections
- Read/Write data across network
- Network debugging
- Network daemon testing
- Simple TCP proxies
- A Socks or HTTP Proxy Command for ssh