Network Scanning
Introduction:
Network scanning is the phase in which the target network is probed in order to find out useful information. Probing a network can bring provide various useful information regarding hosts in the network. With an in-depth scan, the live hosts within the network can be identified, the active and inactive ports, as well as the services running on the ports. Using this information, a map of the network can be created.
TCP Communication:
The Internet Protocol (IP) is a set of rules which govern the routing and addressing of packets of data ensuring that they travel across networks in order to arrive at their correct destination.
IP is of two types:
- TCP
- UDP
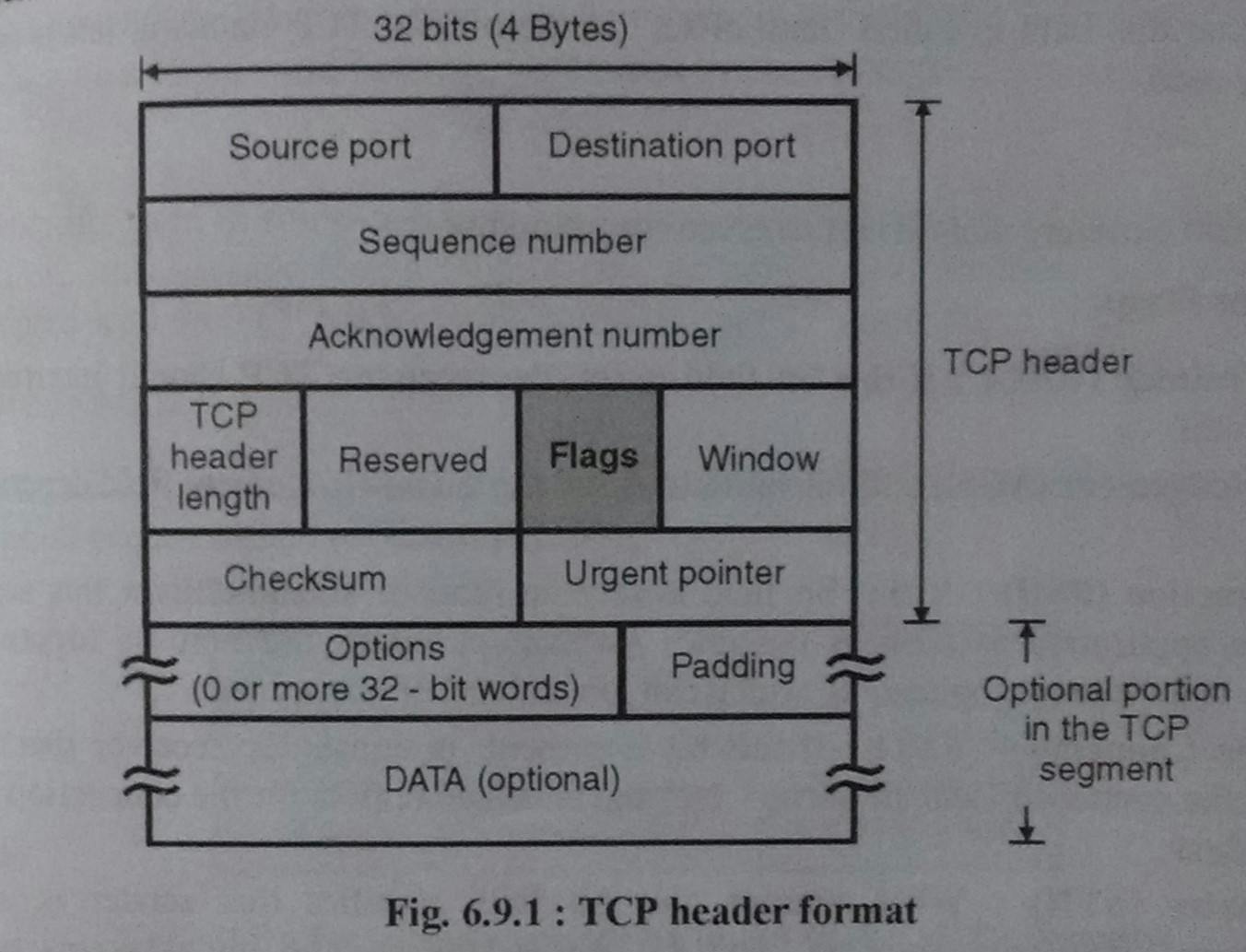
TCP:
The Transmission Control Protocol, is a connection oriented packet protocol, meaning it requires both parties to acknowledge the establishment of the connection for successful communication to take place.The communication is bi-directional. It is reliable and provides error handling and flow-control
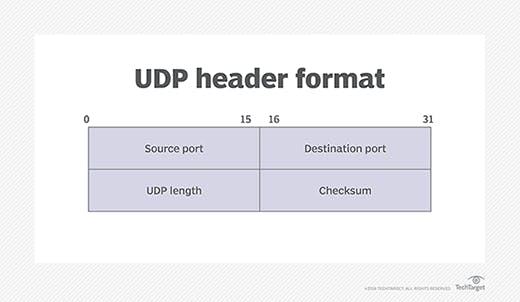
UDP:
User Datagram Protocol is a simpler, connectionless protocol which sends data in chunks in comparison to the TCP. Having fewer headers , it is more lightweight and faster than TCP, which in turn proves less overhead for the network.
TCP flags:

TCP three-way handshake:
In TCP, for two hosts to communicate with each other, a three-way handshake is required. This is a process of establishing the connection between hosts in order to ensure successful, fast, and connection oriented communication. The process is as follows.
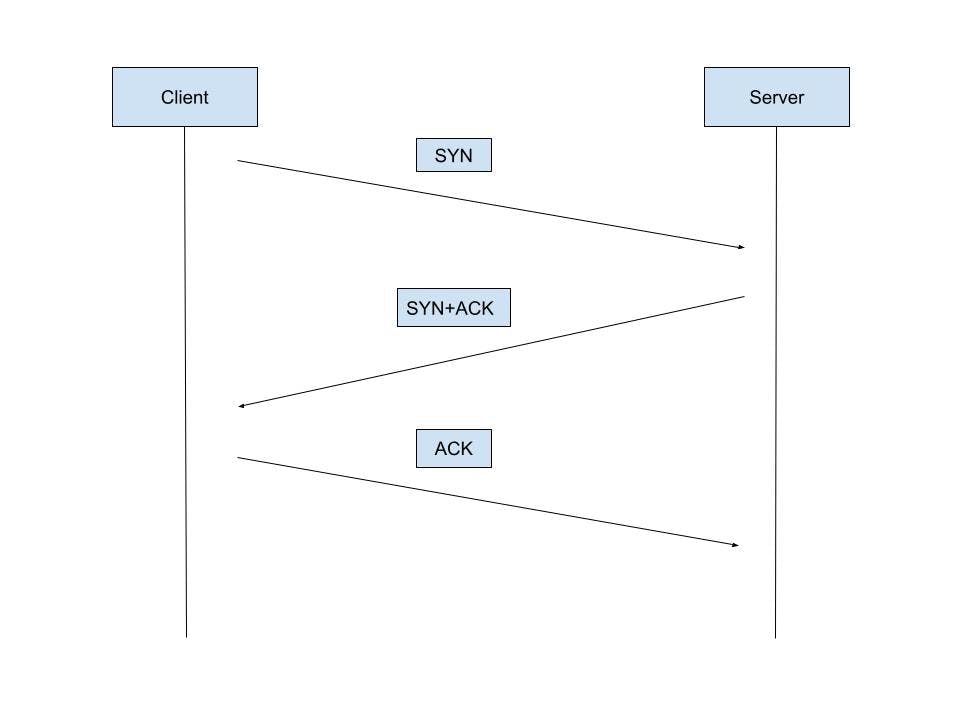
The TCP client first sends a SYN packet to the server as a request to establish connection. The server will respond with a SYN+ACK packet to the client. The client will then respond with an ACK packet in response to the server.
Scanning Methodology:
Scanning methodology includes the following steps:
- Host Discovery
- Port Scanning
- OS fingerprinting / Banner Grabbing
- Vulnerability Scanning
- Network Diagram
- Proxies
Checking for live systems:
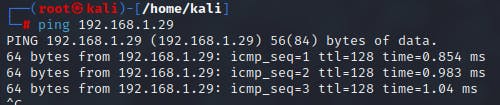
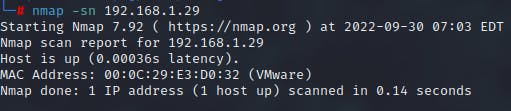
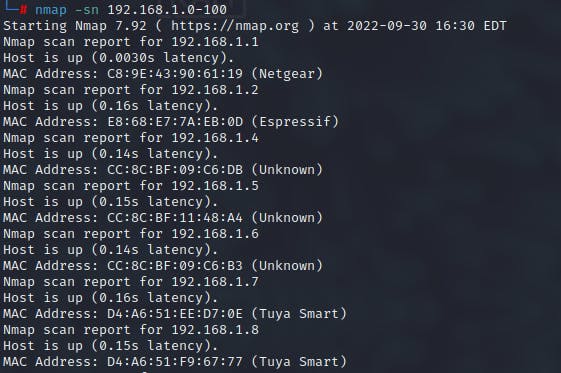
On having connected to a network, the first step is to discovery all the devices which are connected to the network. In order to find the hosts, one possible method is using ICMP packets. ICMP packet are send to the particular IP address. If the host is active, an echo reply is received.
ICMP scanning:
Using ICMP scanning it possible to identify live hosts depending whether or not they reply to the ICMP echo reply packet. Beyond discovery, it can also determine whether the echo packets are passing through firewalls
Ping Sweep:
In order to cover a greater range of IP addresses, using ping sweep is a more efficient way. Rather than individually pinging each host one at a time, using ping sweep, a range of IPs can be pinged to determine the hosts in the network.
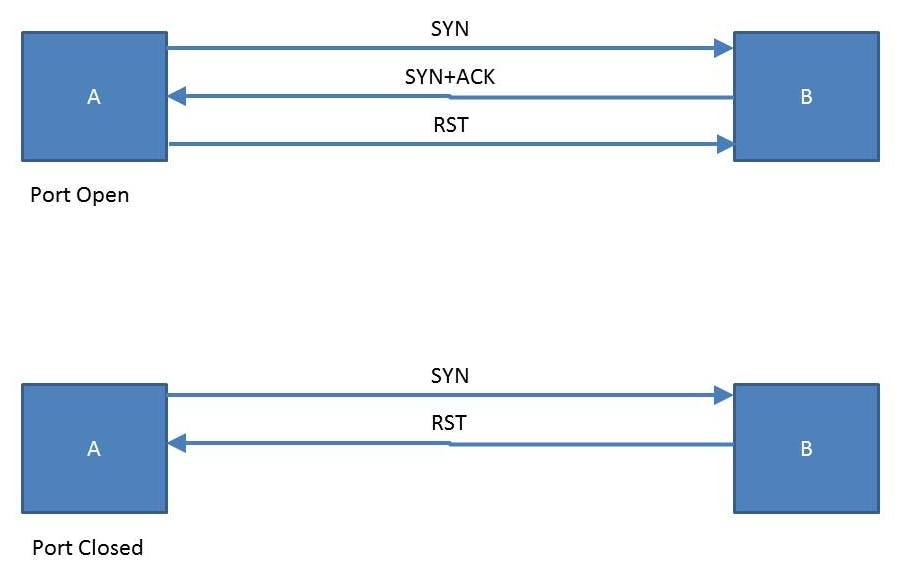
TCP Connect / Full Open Scan
A TCP Connect scan is a unique in which three-way session handshake is initiated and completed. The advantage of this scan is it ensures that the target is live and connection is completed. The same feature can also be a disadvantage as it is can be detected and logged by security devices such as firewalls and IDS.
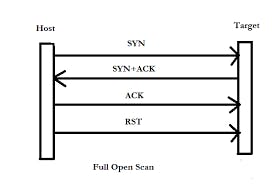
 A closed port responds directly with an RST packet instead of a SYN+ACK packet.
A closed port responds directly with an RST packet instead of a SYN+ACK packet.
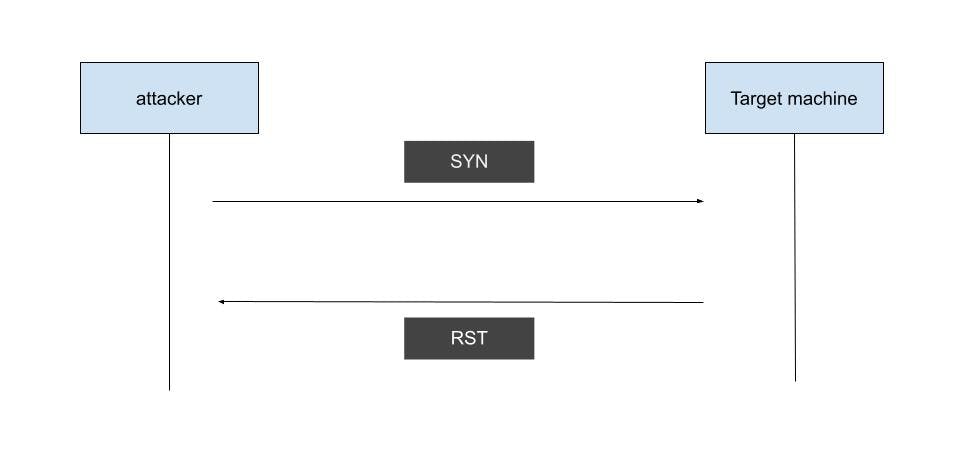
Stealth / Half Open Scan:
As implied in the title, a Half Open Scan sends a SYN packet to the host,and a response SYN+ACK is received. Instead of sending an ACK packet, it directly sends an RST packet, thereby resetting the connection.
The closed port again responds directly with RST packet instead of SYN+ACK packet
Xmas Scan:
This scanning technique send packets with multiple flags - FIN, URG, PSH - to the host. This causes an abnormal situation for the receiver. A closed port will respond with an RST packet. If the port is open, some systems may respond with an open port. However, most modern systems are programmed to ignore or drop these types of packets as they generally are bogus.
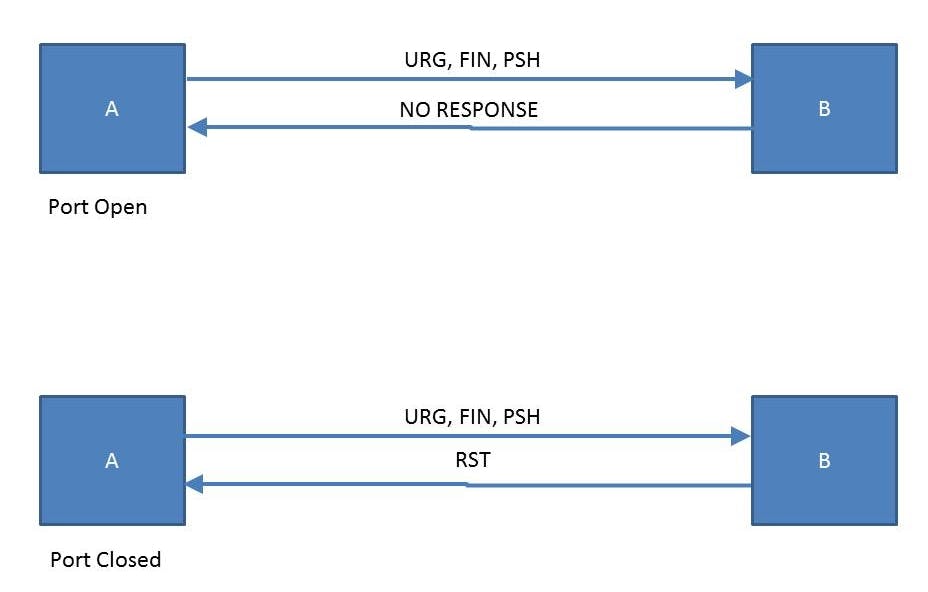
FIN Scan:
A packet with only the FIN flag set can reliably pass the firewall. If the port is open, there will be no response. If the port is closed, RST packet will be send as response.
IDLE / IPID Header Scan:
An IPID Header scan allows the attacker hide its identity behind a zombie system.
Attacker and zombie machine:
- Here, the attacker sends an SYN+ACK packet to the zombie machine.
- As the zombie is not waiting for a SYN+ACK packet, it responds with an RST packet.
- the attacker extracts the IPID from the RST packet
Attacker and target host machine (open port):
- the attacker sends a SYN packet to the target machine with IPID of zombie machine
- the target machine responds to the zombie machine with the SYN+ACK packet if port is open
- the zombie machine responds with RST packet, thereby incrementing the IPID by 1
2.1. Attacker and target machine (closed port):
- the attacker sends a SYN packet to the target machine with IPID of zombie machine
- the target machine responds to the zombie machine with the RST packet if port is closed
Attacker and zombie machine:
- attacker sends SYN+ACK packet to zombie machine
- As the zombie responds with an RST packet.
- IPID disclosed with RST packet.
- IPID is compared with initial number
- port is open if IPID is incremented by 2
UDP Scanning:
Like TCP-based scanning techniques, there are also UDP Scanning methods.
Keeping in mind, UDP is a connectionless protocol. UDP does not have flags. UDP packets are working with ports; no connection orientation requires. No response if the targeted port is open however if the port is closed, the response message of "Port unreachable" returned. Most of the Malicious Programs, Trojans, Spywares uses UDP ports to access the target
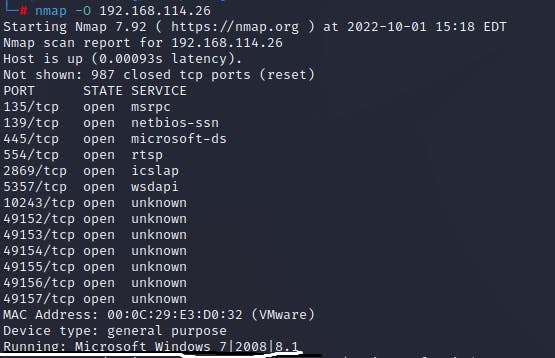
OS Fingerprinting / Banner Grabbing:
OS fingerprinting is a technique of identifying the type of OS a system is running. By identifying the OS, it is possible to determine vulnerabilities and possible bug within the system.
There are two types of OS fingerprinting:
- Active OS fingerprinting
- Passive OS fingerprinting
Active OS fingerprinting:
The Nmap scanner can has many features, one of which is banner grabbing. It sends a TCP or UDP packet to the target system, and observe a detailed response. Within the detailed assessment of the response can show the OS which the host machine is running.
Passive OS Fingerprinting:
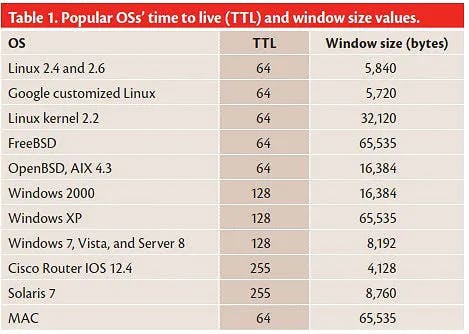
This approach requires a more detailed assessment of the packets. Passive OS Fingerprinting is performed by analyzing the network traffic, specifically the Time To Live(TTL) and TCP Window Size Some common values for operating systems are as follows:
Proxy Server:
A proxy server anonymizes web traffic to provide anonymity. When a user sends a request to a publicly available resource, a proxy server is used an an intermediary in order for these requests. The user request is forwarded to the proxy server, which then forwards the request to the respective servers. Proxy servers are often referred to as web proxy servers. These proxy servers provide access to certain sites which are blocked by IP address blocking.
Uses Proxy server, in a nutshell, can be summarized as:
- Hiding Source IP address for bypassing IP address blocking.
- Impersonating.
- Remote Access to Intranet.
- Redirecting all requests to the proxy server to hide identity.
- Proxy Chaining to avoid detection
Proxy Chaining:
This a technique in which the a request is forwarded to multiple proxy servers one after the other.